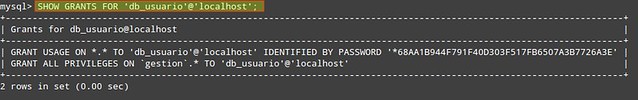
Installation and configuration of a DNS server Using Windows Server 2008
Why we need a DNS Server in LAN (Local Area Network):
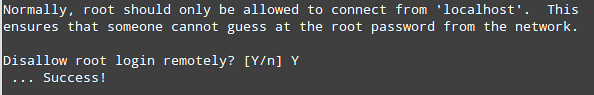
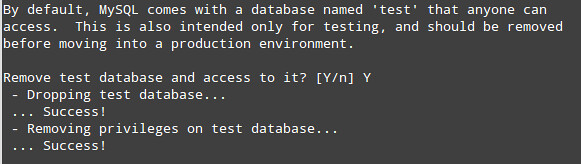
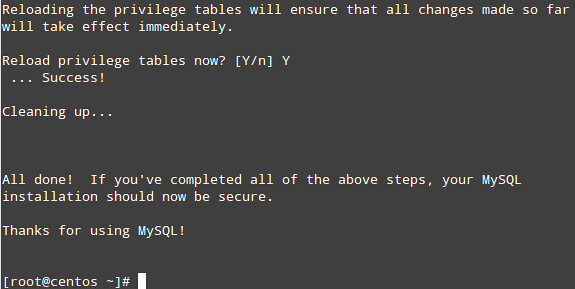
You must know importance of DNS server can be judge from the fact that without DNS, computers would have a very tough time communicating with each other. However, most Windows administrators still rely on WINS for name resolution on local area networks and some have little or no experience with DNS. Steven Warren explains how to install, configure, and troubleshoot a Windows Server 2008 DNS server.
I don't want to go in other details but as many of you are probably aware, the Domain Name System (DNS) is now the name resolution system of choice in Windows (any Microsoft or non Microsoft server). Without it, computers would have a very tough time communicating with each other. However, most Windows administrators still rely on the Windows Internet Name Service (WINS) for name resolution on local area networks and some have little or no experience with DNS. If you fall into this category, read on. We'll explain how to install, configure, and troubleshoot a Windows Server 2008 DNS server.
Installation Step by Step
You can install a DNS server from the Control Panel or when promoting a member server to a domain controller (DC) (Figure A). During the promotion, if a DNS server is not found, you will have the option of installing it.Figure-A

To install a DNS server from the Control Panel, follow these steps:
- From the Start menu, select | Control Panel | Administrative Tools | Server Manager.
- Expand and click Roles (Figure B).
- Choose Add Roles and follow the wizard by selecting the DNS role (Figure C).
- Click Install to install DNS in Windows Server 2008 (Figure D).
Figure B

Expand and click Roles
Figure C

DNS role
Figure D

Install DNS
DNS console and configuration
After installing DNS, you can find the DNS console from Start | All Programs | Administrative Tools | DNS. Windows 2008 provides a wizard to help configure DNS.When configuring your DNS server, you must be familiar with the following concepts:
- Forward lookup zone
- Reverse lookup zone
- Zone types
When selecting a DNS zone type, you have the following options: Active Directory (AD) Integrated, Standard Primary, and Standard Secondary. AD Integrated stores the database information in AD and allows for secure updates to the database file. This option will appear only if AD is configured. If it is configured and you select this option, AD will store and replicate your zone files.
A Standard Primary zone stores the database in a text file. This text file can be shared with other DNS servers that store their information in a text file. Finally, a Standard Secondary zone simply creates a copy of the existing database from another DNS server. This is primarily used for load balancing.
To open the DNS server configuration tool:
- Select DNS from the Administrative Tools folder to open the DNS console.
- Highlight your computer name and choose Action | Configure a DNS Server... to launch the Configure DNS Server Wizard.
- Click Next and choose to configure the following: forward lookup zone, forward and reverse lookup zone, root hints only (Figure E).
- Click Next and then click Yes to create a forward lookup zone (Figure F).
- Select the appropriate radio button to install the desired Zone Type (Figure G).
- Click Next and type the name of the zone you are creating.
- Click Next and then click Yes to create a reverse lookup zone.
- Repeat Step 5.
- Choose whether you want an IPv4 or IPv6 Reverse Lookup Zone (Figure H).
- Click Next and enter the information to identify the reverse lookup zone (Figure I).
- You can choose to create a new file or use an existing DNS file (Figure J).
- On the Dynamic Update window, specify how DNS accepts secure, nonsecure, or no dynamic updates.
- If you need to apply a DNS forwarder, you apply it on the Forwarders window. (Figure K).
- Click Finish (Figure L)
Figure E

Figure F

Forward lookup zone
Figure G

Desired zone
Figure H

IPv4 or IPv6
Figure I
Reverse lookup zone
Figure J

Choose new or existing DNS file
Figure K

Forwarders window
Figure L

Now installation is finished. From here we will start configuring DNS server for connectivity of your client and other services to resolve naming.
Managing DNS records
You have now installed and configured your first DNS server, and you're ready to add records to the zone(s) you created. There are various types of DNS records available. Many of them you will never use. We'll be looking at these commonly used DNS records:- Start of Authority (SOA)
- Name Servers
- Host (A)
- Pointer (PTR)
- Canonical Name (CNAME) or Alias
- Mail Exchange (MX)
Start of Authority (SOA) record
The Start of Authority (SOA) resource record is always first in any standard zone. The Start of Authority (SOA) tab allows you to make any adjustments necessary. You can change the primary server that holds the SOA record, and you can change the person responsible for managing the SOA. Finally, one of the most important features of Windows 2000 is that you can change your DNS server configuration without deleting your zones and having to re-create the wheel (Figure M).Figure M

Change configuration
Name Servers
Name Servers specify all name servers for a particular domain. You set up all primary and secondary name servers through this record.To create a Name Server, follow these steps:
- Select DNS from the Administrative Tools folder to open the DNS console.
- Expand the Forward Lookup Zone.
- Right-click on the appropriate domain and choose Properties (Figure N).
- Select the Name Servers tab and click Add.
- Enter the appropriate FQDN Server name and IP address of the DNS server you want to add.
Figure N

Name Server
Host (A) records
A Host (A) record maps a host name to an IP address. These records help you easily identify another server in a forward lookup zone. Host records improve query performance in multiple-zone environments, and you can also create a Pointer (PTR) record at the same time. A PTR record resolves an IP address to a host name.To create a Host record:
- Select DNS from the Administrative Tools folder to open the DNS console.
- Expand the Forward Lookup Zone and click on the folder representing your domain.
- From the Action menu, select New Host.
- Enter the Name and IP Address of the host you are creating (Figure O).
- Select the Create Associated Pointer (PTR) Record check box if you want to create the PTR record at the same time. Otherwise, you can create it later.
- Click the Add Host button.
Figure O
To ad a Host (A) record
Pointer (PTR) records
A Pointer (PTR) record creates the appropriate entry in the reverse lookup zone for reverse queries. As you saw in Figure H, you have the option of creating a PTR record when creating a Host record. If you did not choose to create your PTR record at that time, you can do it at any point.To create a PTR record:
- Select DNS from the Administrative Tools folder to open the DNS console.
- Choose the reverse lookup zone where you want your PTR record created.
- From the Action menu, select New Pointer (Figure P).
- Enter the Host IP Number and Host Name.
- Click OK.
Figure P

New Pointer
Canonical Name (CNAME) or Alias records
A Canonical Name (CNAME) or Alias record allows a DNS server to have multiple names for a single host. For example, an Alias record can have several records that point to a single server in your environment. This is a common approach if you have both your Web server and your mail server running on the same machine.To create a DNS Alias:
- Select DNS from the Administrative Tools folder to open the DNS console.
- Expand the Forward Lookup Zone and highlight the folder representing your domain.
- From the Action menu, select New Alias.
- Enter your Alias Name (Figure Q).
- Enter the fully qualified domain name (FQDN).
- Click OK.
Figure Q

Alias Name
Mail Exchange (MX) records
Mail Exchange records help you identify mail servers within a zone in your DNS database. With this feature, you can prioritize which mail servers will receive the highest priority. Creating MX records will help you keep track of the location of all of your mail servers.To create a Mail Exchange (MX) record:
- Select DNS from the Administrative Tools folder to open the DNS console.
- Expand the Forward Lookup Zone and highlight the folder representing your domain.
- From the Action menu, select New Mail Exchanger.
- Enter the Host Or Domain (Figure R).
- Enter the Mail Server and Mail Server Priority.
- Click OK.
Figure R

Host or Domain
Other new records
You can create many other types of records. For a complete description, choose Action | Other New Records from the DNS console (Figure S). Select the record of your choice and view the description.Figure S

Create records from the DNS console
Troubleshooting DNS servers
We will not going in depth to tell you about troubleshooting perhaps troubleshooting DNS servers, the nslookup utility will become your best friend. This utility is easy to use and very versatile. It's a command-line utility that is included within Windows 2008. With nslookup, you can perform query testing of your DNS servers. This information is useful in troubleshooting name resolution problems and debugging other server-related problems. You can access nslookup (Figure T) right from the DNS console.Figure T

Thanks for reading, must your inputs regarding my this blog post ....